TryHackMe - Advent of Cyber 2 Part 4
TryHackMe room write-up: Advent of Cyber 2 (days 20 - end: Blue Teaming and Finale )
Is that the finish line in sight??
Day 20: PowershELlf to the rescue
Oh hey theres actually (potentially) more scripting since we are taking a look at powershell today. I hadn’t really touched powershell prior to my current job, I still have tons to learn about it but it’s a very powerful tool (and I would like to become familiar with PowerShell Empire).
PowerShell is pretty slow when running over SSH but by sheer determination (and spamming Get-Content, Get-ChildItem, Set-Location, and Select-String commands) I was able to find these answers:
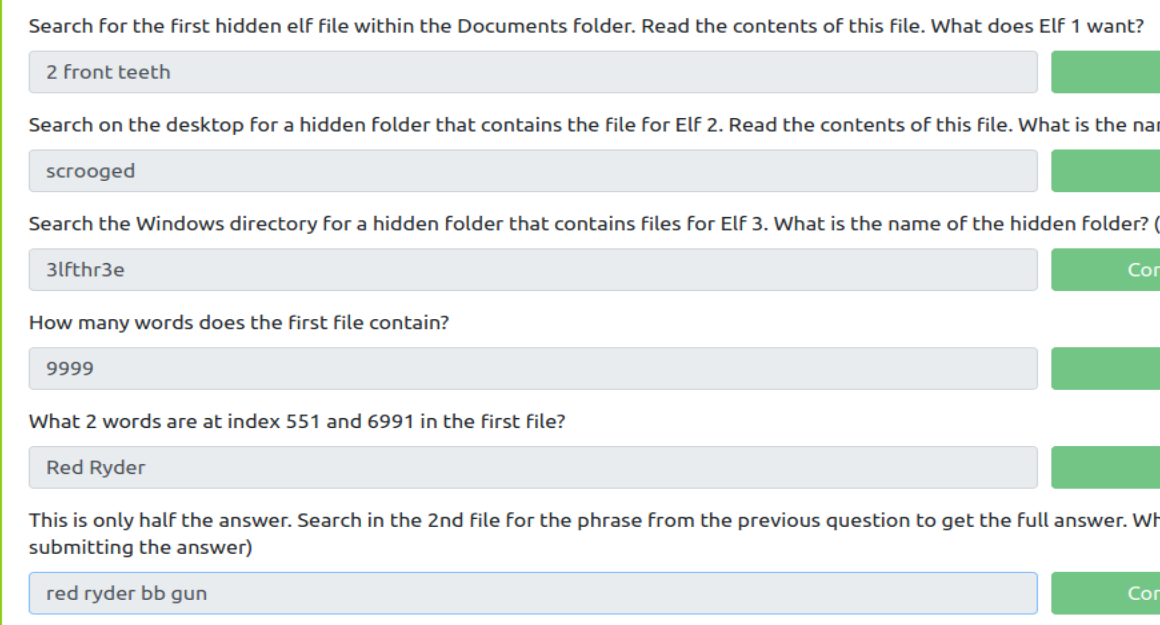
Day 21: Time for some ELForensics
Carrying on with PowerShell, we are taking a look at more advanced commands that we can use in PowerShell. For the questions we have to get file hashes, analyze some executables and get an understanding of a file’s ADS (Alternate Data Stream).
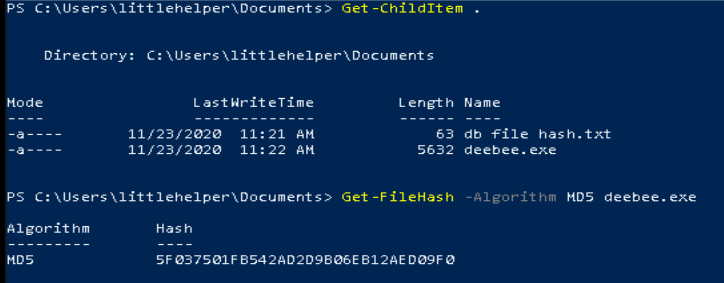
By using these methods, we can establish that the ‘db file hash.txt’ file and deebee.exe have different MD5 hashes and are not the same.
I solved the last question using this command:
wmic process call create $(Resolve-Path .\deebee.exe:hidedb)
Day 22: Elf McEager becomes CyberElf
Today, we will be regaining access to a password manager. Breaking into a password manager is a little ironic but I’m sure it happens more often than not.
This challenge introduced me to cyberchef, the self proclaimed Cyber Swiss-Army knife (and with good reason). It’s a pretty handy tool that can be used to decrypt/decode data. The fully working online repo can be found here: https://gchq.github.io/CyberChef/
In order to find the flag in this room, the node section had this:
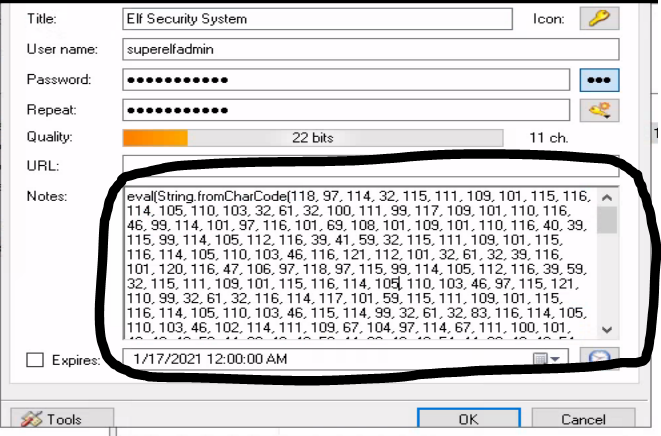
We can use cyberchef to decode charcode and we get this as the result
https://gist.github.com/heavenraiza/1d321244c4d667446dbfd9a3298a88b8
Note: Make sure you select the proper delimiter before running the decode function.
Day 23: The Grinch strikes again
Ooh, now we have to take a look at ransomware. We must do our duty as a blue teamer and save the workstations.
The first tool that we are taking a look at today is vss, or volume shadow copy service. This tool built in to windows attempts to create a consistent shadow copy so that backups are not lost (it is stated in this challenges description that malware authors are very aware of its existence). VSS is best paired with task scheduler. Lets see what we are dealing with:

A fitting wallpaper for the previous year for sure. Another tool we are going to need to fix this is Disk Management
This ransomware allowed a lot of freedom so it was not super difficult to restore from backups and recover the necessary password files.
Day 24: The Trial Before Christmas
Here it is the big finale, I decided to skip the walkthrough and try to see if I could cross the finish line. I opened with an nmap scan of the target:
nmap --top-ports 1000 -sV {MACHINE IP}
This showed that two apache 2.4.29 webservers for ubuntu were running out of port 80 and port 65000. The port 80 website looks like a clone of tryhackme. The other one looked like this:
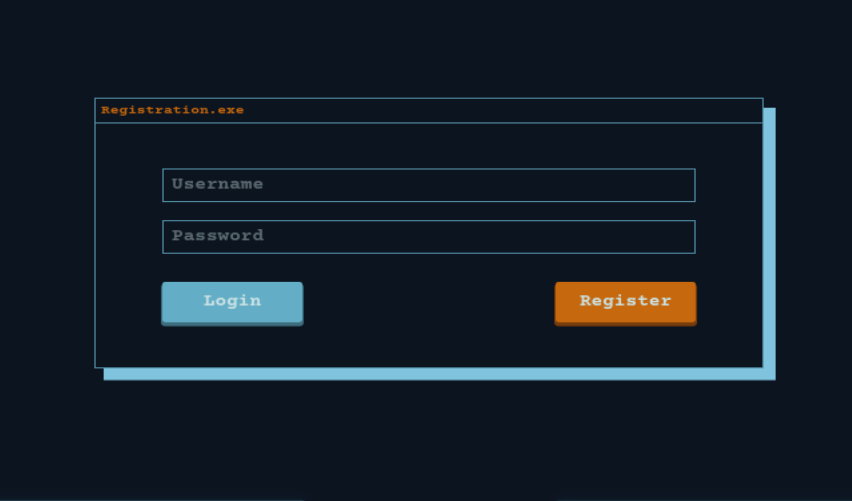
So the secret application is called life cycle, I ran gobuster with a .php extension to see if I could find the hidden php page:
gobuster dir -u http://{MACHINE IP}:65000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php
At first I was using rockyou.txt which was not returning anything so I switched to one of the generic directory lists and it answered the next two questions:
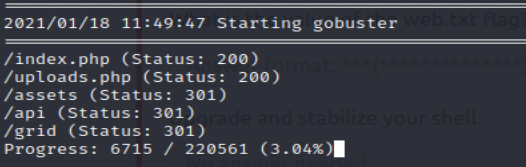
Taking a look at the pages source it looks like it will accept image uploads, I tried a double-barreled extension witha php reverse shell payload off the rip and it didnt work lol. I looked at the source and found some js files that were pretty insightful:
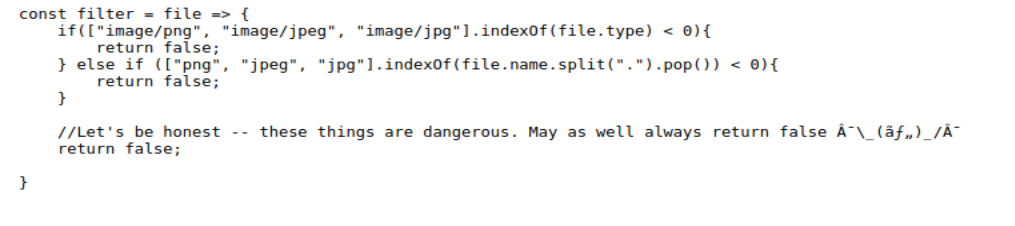
filter.js:
upload.js:
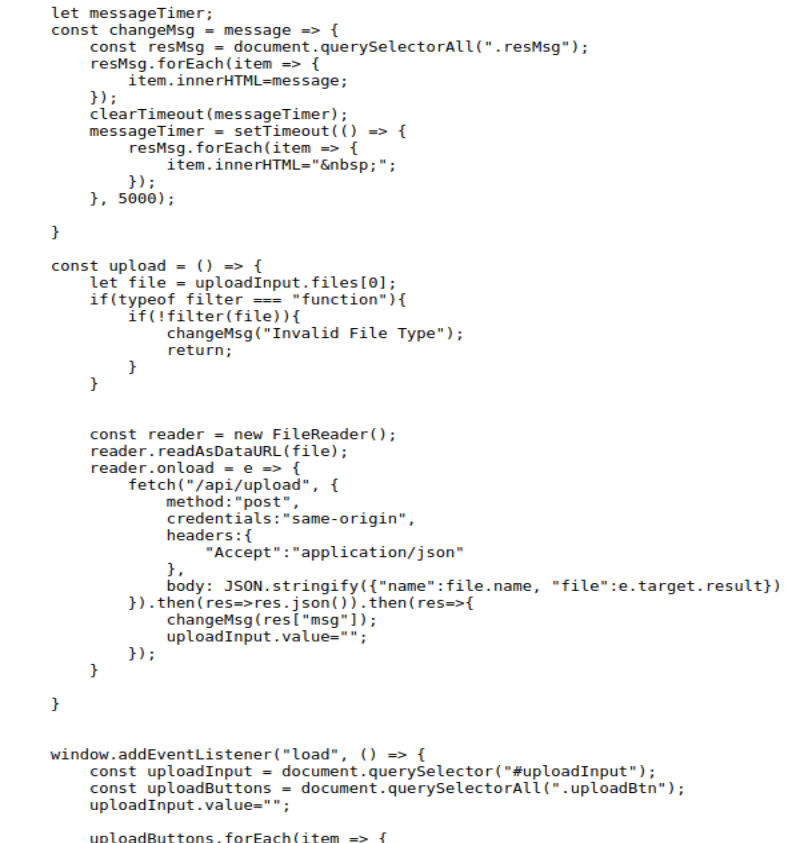
So it looks like it’s set to filter everything on the client-side too. The solution to this(I had to reference the supporting material here) is to load the page while not accepting the filter.JS using burpsuite. After bypassing the client-side filter NOW we can do the double barrel extension to bypass the server-side filter.
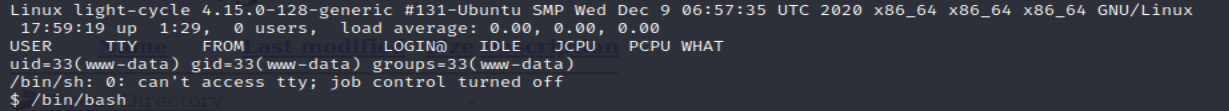
Now its time to get to work! I made the shell stable using python and began looking for the flags. I used the mysql database in order to find the user flynn on the system and cracked his hash.
Now the last part was wild. In order to escelate priveleges to root, the room has us spin up lxd which is similar to docker in that it creates containers which can be run by individuals in the lxd group. By creating a container, setting the mount point to roots directory and executing the container we are able to leverage a flaw in lxd and become root. I had no idea this was a thing and it was super cool. This conlcudes the Advent of Cyber 2 challenge, congrats on making it to the end!