TryHackMe - Advent of Cyber 2 Part 3
TryHackMe room write-up: Advent of Cyber 2 (days 13 - 19: Topic Variety Pack! )
Day 13: Coal For Christmas
This days challenge was a special room created by John Hammond. I recommend you go check out his youtube channel if you haven’t, he has a lot of insightful content related to cybersecurity and CTF’s. At first glance of the content, it looks like we are going to be performing some kernel exploits.
nmap -sV {Machine IP}
The results of this scan show us that three ports are open: 22, 23, and 111. Since Telnet is running out of port 23 and Telnet is also a depreciated service. Let’s connect to it.
telnet {Machine IP} 23
After logging in, the very first thing I did was escape the awful shell hell by running /bin/bash. Then I checked the OS + version info and found this machine is running Ubuntu 12.04. You smell that? It smells like a dirty cow or something…
I grabbed the dirty cow exploit from github and spun up a python http server so I could download it from the target machine. In the source of dirty.c we are provided with instructions on how to properly compile this exploit:
gcc -pthread dirty.c -o dirty -lcrypt
Now we run the exploit, here is what the start of it looks like:
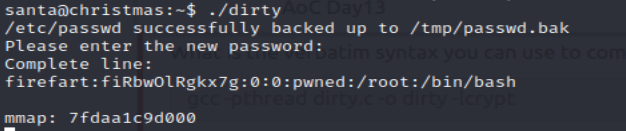
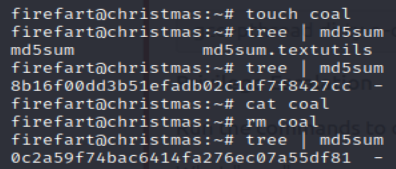
You have to wait a bit, but it does create a new user with the password you pass through the compiled program. This new user has root privelages, it’s a pretty neat exploit for sure. I thought the last question was pretty neat as well. In order to get the flag we have to create a file named “coal”, run a tree command and pipe the output of that command to print the md5 checksum. We only get the right flag if the file “coal” exists and no other content in the /root directory is altered:
Day 14: Where’s Rudolph?
This days challenge revolves all around OSINT. Funny thing happened before starting this room, I made my first twitter account earlier today(I’m not the biggest fan of social media and it’s only to follow security-related topics/individuals) but while I was following people I actually stumbled across “Rudolphs” twitter account mentioned in the challenge. It’s a small world I guess.
Since showing all the answers would ruin the fun of OSINT, I’ll leave this one up to you reader :). I will say it’s really handy to have a local copy of an exif-tool on your machine, its a really great alternative to online tools.
Day 15: There’s a Python in my stocking!
We got python scripting today! After you get used to the necessary indentation/white-space requirements, Python is a pretty neat scripting language!
NOTE TO SELF: “Now let’s say we wanted to add this variable to another variable. A common misconception is that we take the bucket itself and use that. But in Python, we don’t. We pass by reference. As in, we merely pass a location of the variable — we do not pass the variable itself. The alternative is to pass by value. This is very important to understand, as it can cause a significant amount of headaches later on.”
Day 16: Help! Where is Santa?
Only two days worth of scripting (big sad :’( ) so part 2 of 2 here we go. We have to find the correct API key with the following rules:
The key for the API is between 0 and 100, and it’s an odd number. But be careful! After an unknown number of attempts, Santa’s Sled will ban your IP address.
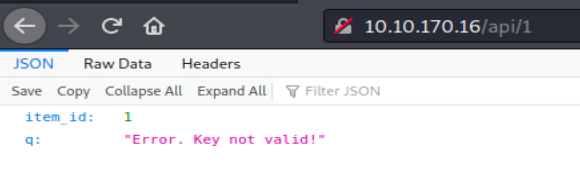
So I first tested the api with the number one just to see what would happen:
A little scripting later and I came up with this:
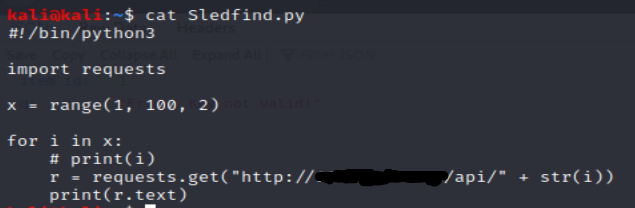
I just kind of hoped I wouldn’t send too many requests and let it run. Here’s what I found:
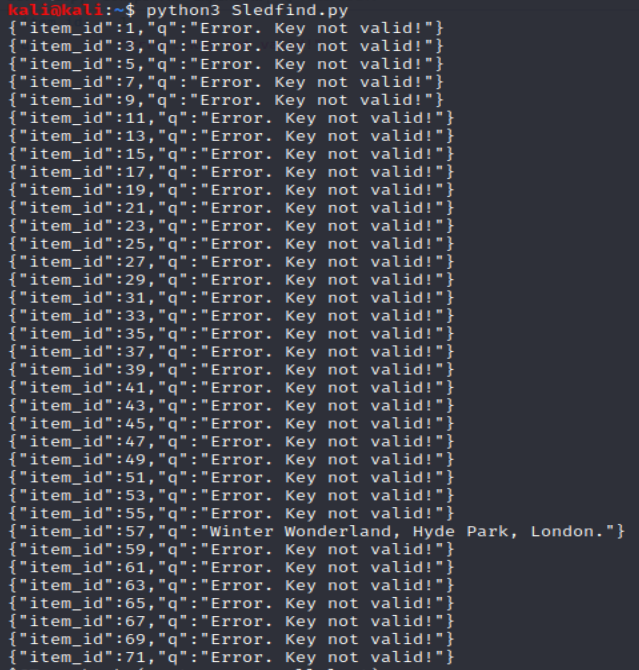
aaaaand thats all the scripting challenges (big sad intensifies).
Day 17: ReverseELFneering
No more sadness because it’s time to do some reversing! As of writing this, I have worked on very little on reverse engineering challenges/research but I’m very interested in this topic in particular.
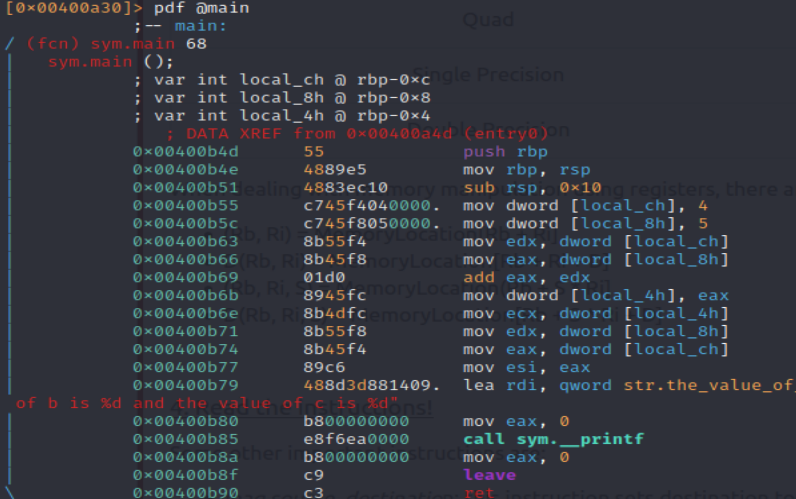
Just going to leave this here… https://scoding.de/uploads/r2_cs.pdf
The entire guide was a really good read on radare2, which I have used a couple times in the past.
General workflow when via r2 commands looks like this
r2 -d <PROGRAM/BINARY> –> aa (to analyze said program) –> afl (list out the parts it found) –> pdf @(function) (to print disassembely function)
then ‘db’ will determine a breakpoint, ‘dc’ will run the program until breakpoints are hit, ‘px @mem-addr’ will view that memory address, and ‘ood’ will reload the program in case we screw up. When in doubt debug line by line
Day 18: The Bits of Christmas
Oh hey hey, it looks like we are taking a look under the hood of a .net application on this days challenge. Two new applications are introduced in this days description that I have never heard of before: ILSpy and Dotpeek.
After passing the Program through ILSpy, I peaked at the main function I was able to get all the info necessary to answer the questions (wink wink nudge nudge)
Day 19: The Naughty or Nice List
Day 19 is a special by Tib3rius and it covers the topic of Server-Side Request forgery. SSRF is, in essence, forcing a server to request something that it (in the scope of that application) would not usaully request. The example that was given was a website that has the function of returning an image of other websites if it is supplied with a URL. If the attacker supplies URLs for internal IP addresses or host names, they could potentially leak sensitive information.
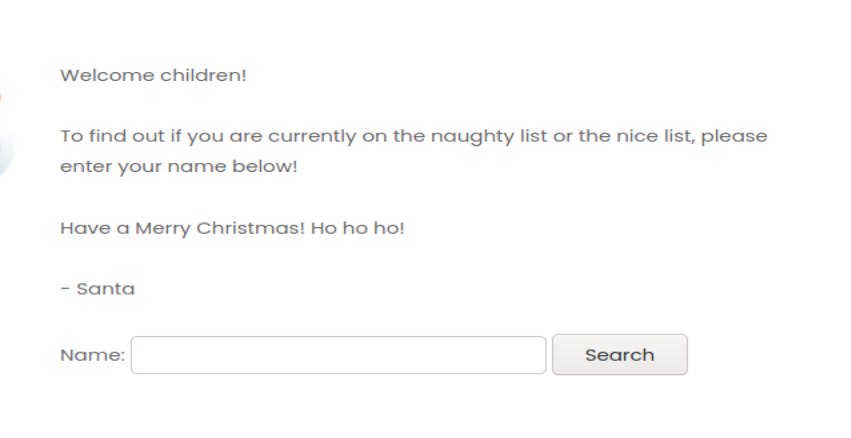
The webpage that was served up had a field for user input. I ran burp to intercept this request and see what I could get.
/?proxy=http%3A%2F%2Flist.hohoho%3A8080%2Fsearch.php%3Fname%3Dtest
So this is the resource its trying to get. I converted the URL encoded characters to make this readable: /?proxy=http://list.hohoho:8080/search.php?name=test
Then I just started editing the GET parameters until I got all the info necessary, the supporting material gave the answer on how to view localhost. if you need a Subdomain that resolves to 127.0.0.1 but don’t want to register one, you can use localtest.me which always resolves to localhost.