Crackme4
CrackMe 4: StrCmp reversal
I was working through some ELF crackmes on tryhackme, here is the room link. The fourth challange is where this got interesting. I fired up ghidra and started to take a look at the binary.
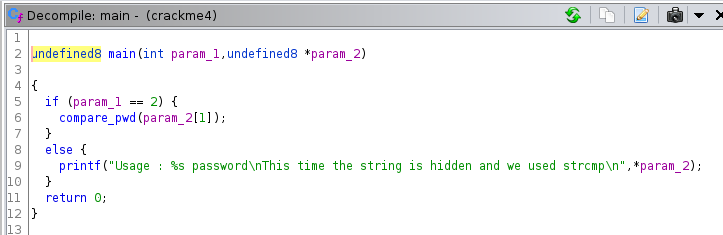
So the main function is really simple. There is a call to a function called compare_pwd. We can conclude by the if statement of the main function that we will use some comparison operation to tell if the user supplies a correct password or not. I then went to the compare_pwd function to take a look:
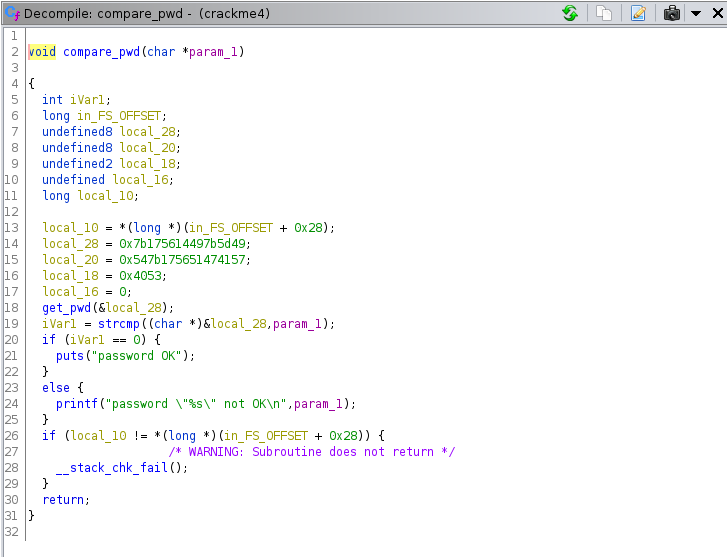
So judging by the strcmp function, we need to swipe the value of var28h. I had some trouble running the ghidra debugger so I instead fired up radare2.
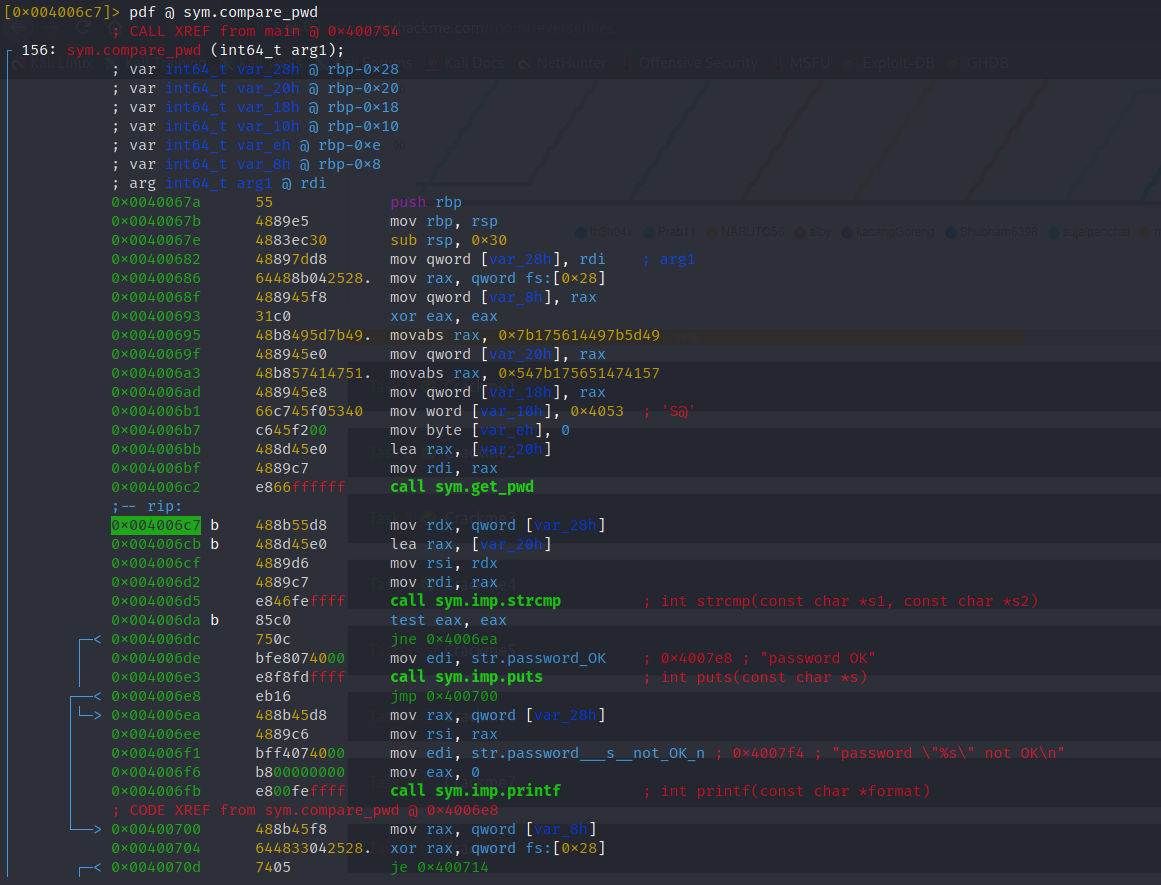
After setting a few breakpoints, I was able to view value of var28h and just like that: